Deactivate Vulnerable Protocols
If your servers support older protocols such as TLS 1.0 and TLS 1.1, this will be listed as a vulnerability in the reports we deliver to you.
These are included because the protocols are no longer considered secure.
The figure below shows the vulnerable protocols we have found on a particular server
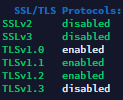
All modern browsers support the newer and more secure protocols. However, you should be aware that there may be older clients connecting to your server that do not necessarily support the newer protocols. This is typically seen when there are some embedded systems that need to connect to your servers.
To disable these protocols, changes must be made to the server’s registry.
Below are three methods to disable them: manually, via a script, and via a program.
Please note that the setting applies to the entire server and not just a single website. Make sure to have a valid backup of the server or the registry in case the settings need to be reverted.
Manually
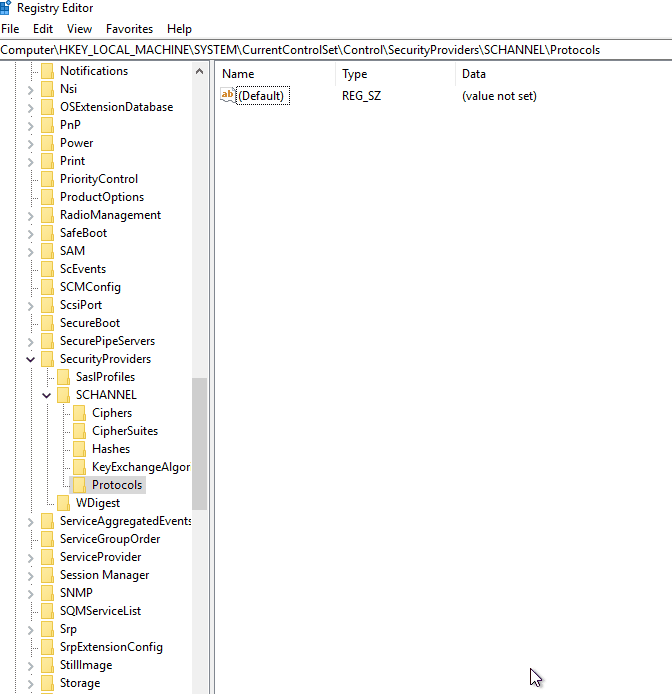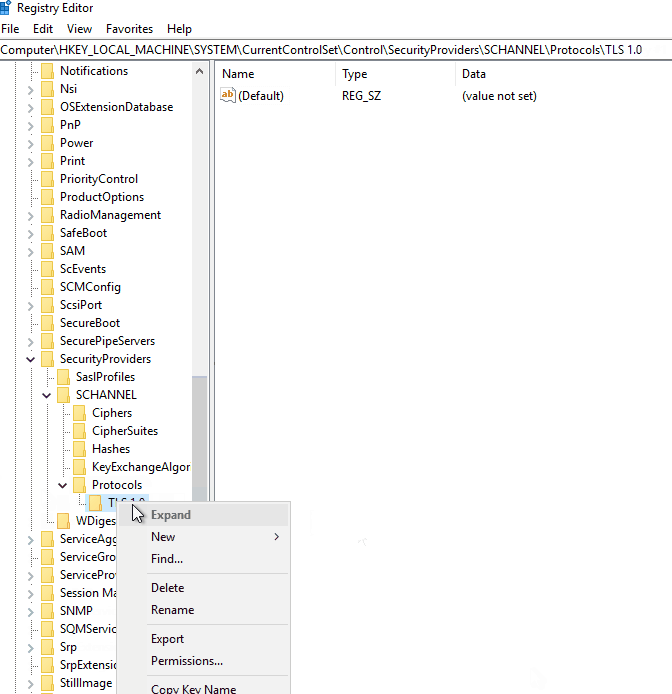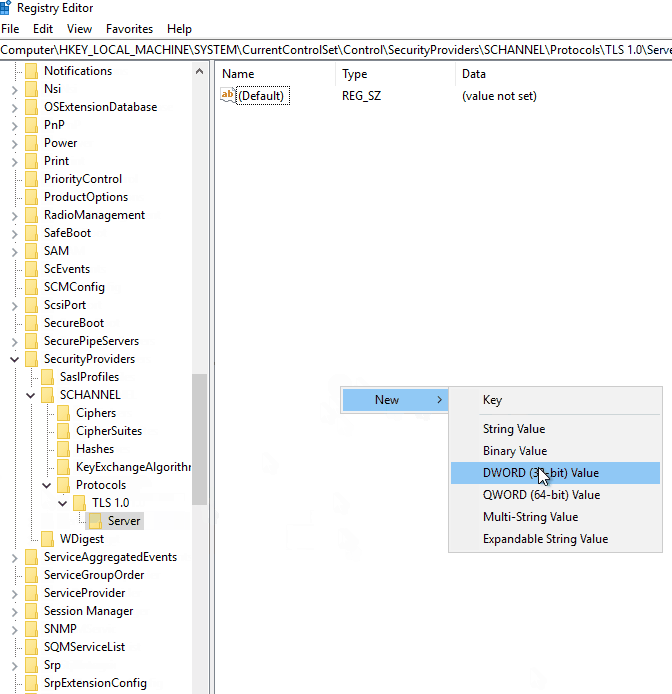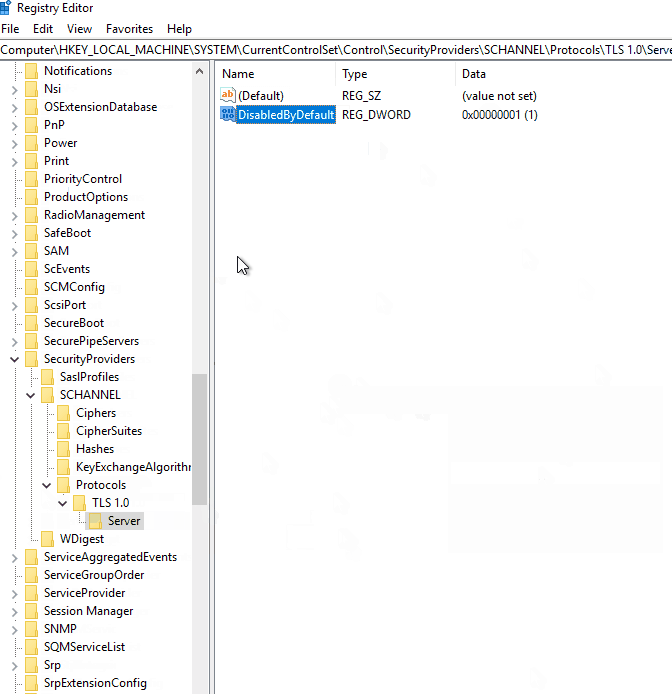
Open the Registry Editor
Perform a backup of the registry.
If you need to restore the registry, the machine may need to be rebooted into safe mode, because there are some values that cannot be overwritten while the system is running.
Navigate to HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Control\\SecurityProviders\\SCHANNEL\\Protocols
Create the two subkeys “TLS 1.0\\Server” if they do not already exist. Create a registry key named “DisabledByDefault” and set the DWORD value to 1.
Do the same for TLS 1.1, but replace the subkey folder with “TLS 1.1” instead of “TLS 1.0.”
If older versions such as SSLv2 or SSLv3 are supported, they can be disabled by doing the same in the “SSL 2.0” and “SSL 3.0” folders.
Restart the servers.
Powershell
Open a powershell console
Run the following command to disable TLS 1.0 in the same way we did manually above.
[microsoft.win32.registry]::SetValue(“HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Control\\SecurityProviders\\SCHANNEL\\Protocols\\TLS 1.0\\Server”, “DisabledByDefault”, 1)
Run the following command to disable TLS 1.1
[microsoft.win32.registry]::SetValue(“HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Control\\SecurityProviders\\SCHANNEL\\Protocols\\TLS 1.1\\Server”, “DisabledByDefault”, 1)
Restart the servers.
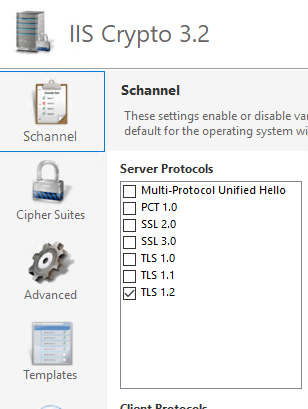
IIS crypto
Download IIScrypto fra www.nartac.com
Run IIS crypto on the server.
Make sure to remove the checkmark from TLS 1.0 and TLS 1.1 and click apply
Restart the server