Terminal Services Doesn’t Use Network Level Authentication (NLA) Only
**Disclaimer**: Please note that the following actions involve making changes to your system. We provide this information for guidance purposes only. We are not responsible for any damage or loss that may occur as a result of implementing these steps. It is recommended to proceed with caution and have a valid backup of your server before making any modifications.
Vulnerability Details
The remote Terminal Services is currently not set to exclusively use Network Level Authentication (NLA). NLA employs the Credential Security Support Provider (CredSSP) protocol for robust server authentication, utilizing either TLS/SSL or Kerberos methods to safeguard against man-in-the-middle attacks. Beyond enhancing authentication processes, NLA additionally secures the remote computer from harmful users and software by ensuring user authentication is finalized before establishing a complete RDP connection.
Severity Rating
Medium
How to Verify if a Device is Vulnerable
Use Nessus plugin ID 58453 to scan the device for the vulnerability.
How to Fix
Enable Network Level Authentication (NLA) on the remote RDP server. This is generally done on the ‘Remote’ tab of the ‘System’ settings on Windows.
Guide
Enabling via remote desktop settings:
To access Windows Settings, press the “Win + I” keys together. Then, click on “System.” Scroll down in this section until you find “Remote Desktop” listed in the left-side menu. Click on it, and then turn on the “Remote Desktop” option. Finally, click “Confirm” when the confirmation prompt appears.
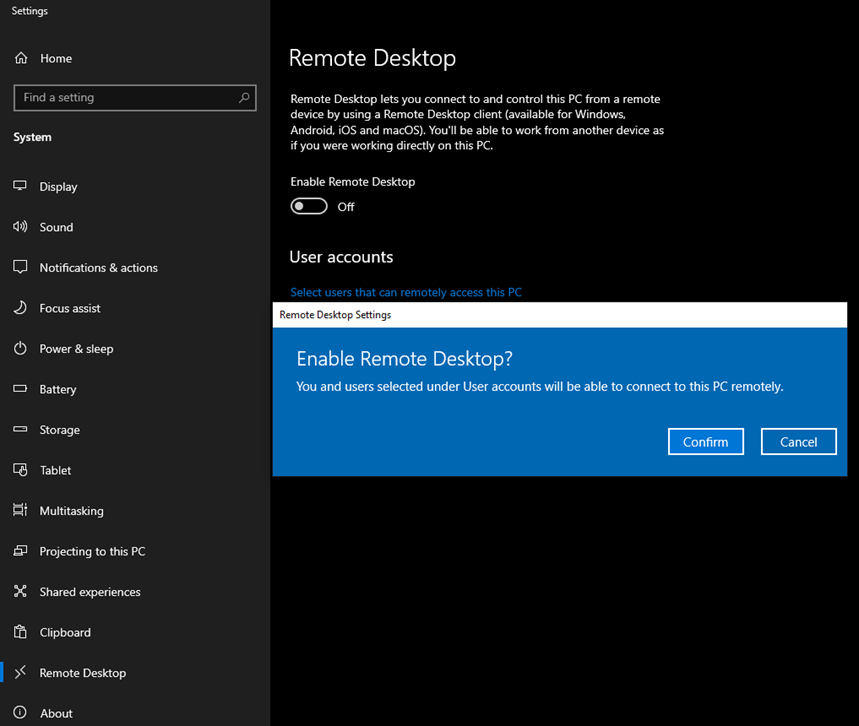
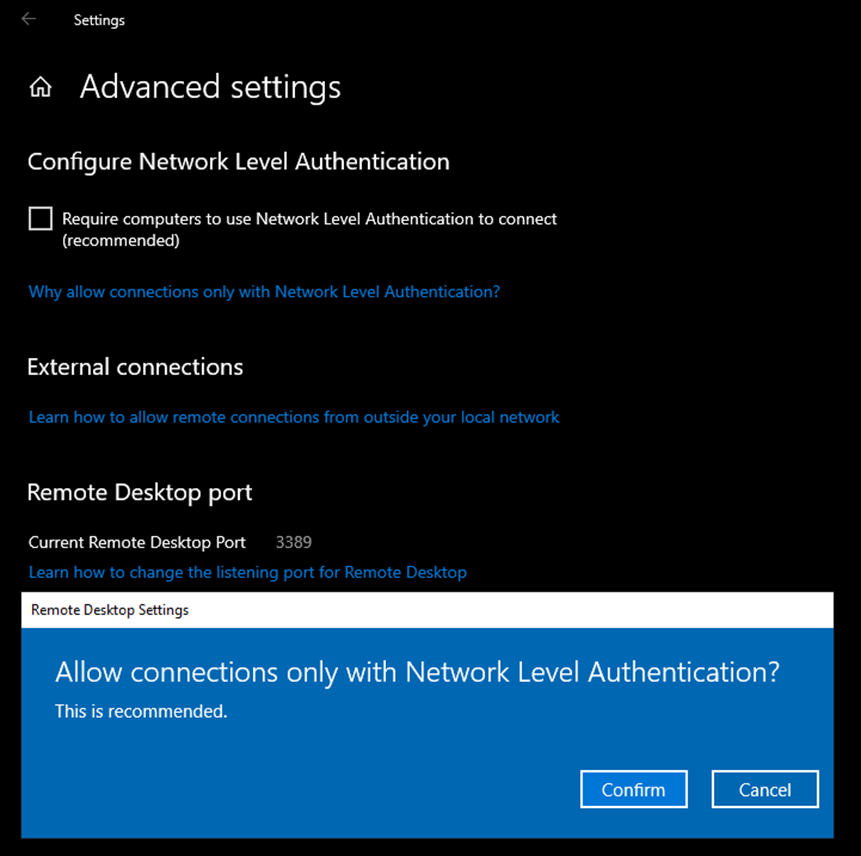
After activating “Remote Desktop,” select “Advanced Settings.” In the following screen, make sure to choose the option “Require computers to use Network Level Authentication to connect (recommended)” to enable Network Level Authentication (NLA).
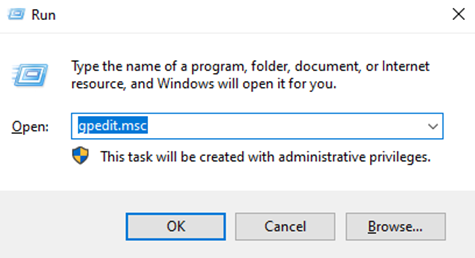
Enabling via Local Group Policy editor
Start by opening the Group Policy Editor. You can do this by typing ‘gpedit’ into the search or run dialog.
Go to the following location in the settings:
Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Security.
Double-click on the option titled “Require user authentication for remote connections by using Network Level Authentication.”
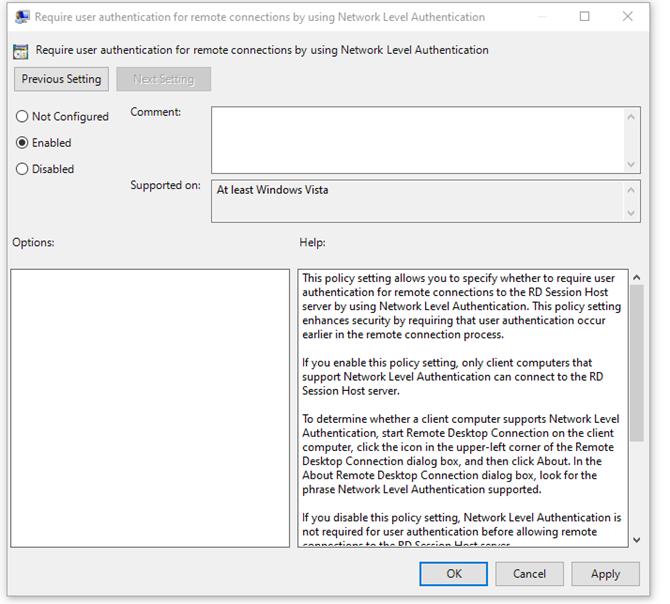
Select ‘Enabled’, then click ‘Apply’ and ‘Save’. Please note that a reboot is required for the changes to take effect.
Rollback
Using registry
Begin by opening “Run” on Windows, which can be done by pressing the “Win + R” keys together. In the Run box, enter “regedit” and press Enter. This action will open the Registry Editor on your Windows system.
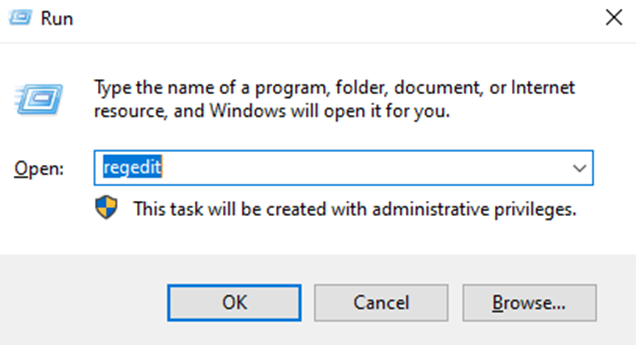
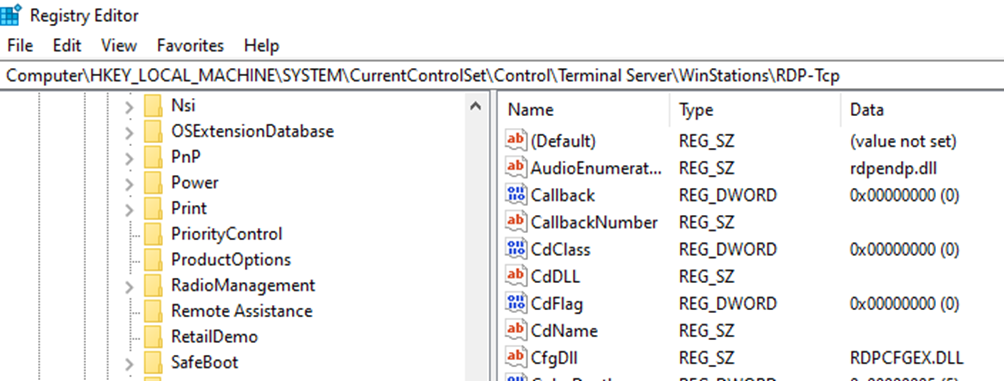
After opening the Registry Editor, proceed to the following path: “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp”.
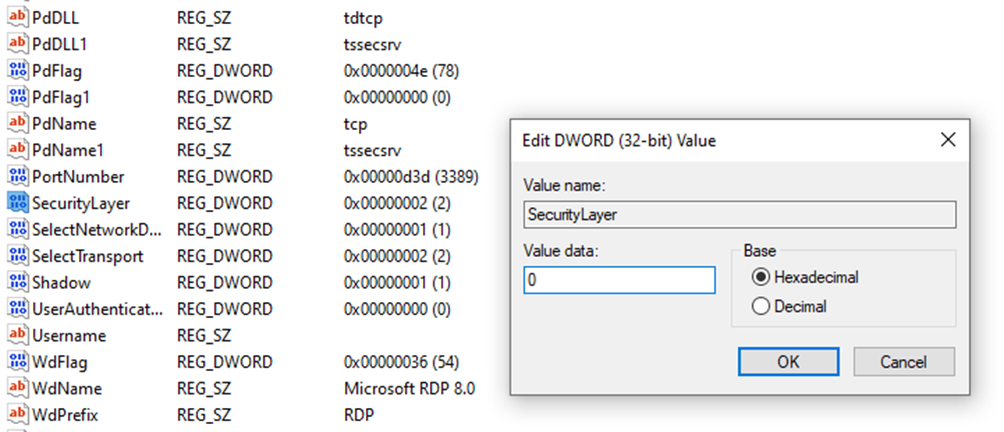
Locate the “SecurityLayer” and “UserAuthentication” keys. Modify the data values to “0” to turn off Network Level Authentication (NLA). For these changes to take full effect, restart your computer.
How to Verify the Fix
- Rescan the device with Nessus plugin ID 58453 and check for the vulnerability.
- Or you can use rdesktop to try connecting, use the following command:
rdesktop <IP> if you enabled NLA you should get the following response: Failed to connect, CredSSP required by server.
Preventative Measures
Ensure that NLA (Network Level Authentication) is activated on the standard image used for deploying new servers.

